PowerCLI 13.1 introduces two new auto generated modules that provide PowerShelI bindings for the vSphere Replication REST API and the Site Recovery Manager REST API. We will cover connection management for both modules – host based replication with vSphere Replication and creation of protection groups and recovery plans with Site Recovery Manager.
Connecting vSphere Replication server with Connect-VrServer
To connect to a vSphere Replication management server you must use the Connect-VrServer cmdlet. Replications can be configured within a single vCenter Server, or between local and remote vCenter Server instances.
When configuring replication within the same VC you can connect only to the local vSphere Replication site. For Server parameter specify the vSphere Replication server address. For User and Password parameters specify the user name and the password for the vCenter Server instance where the vSphere Replication appliance is deployed:
$vrConnection = Connect-VrServer -Server "MyVrAddress.com"
-User "administrator@vsphere.local" `
-Password "MyLocalVCenterServerPassword"
Let’s take a moment and look at the VrServerConnection object, returned from the Connect-VrServer cmdlet. It contains ConnectedPairings property:
![]()
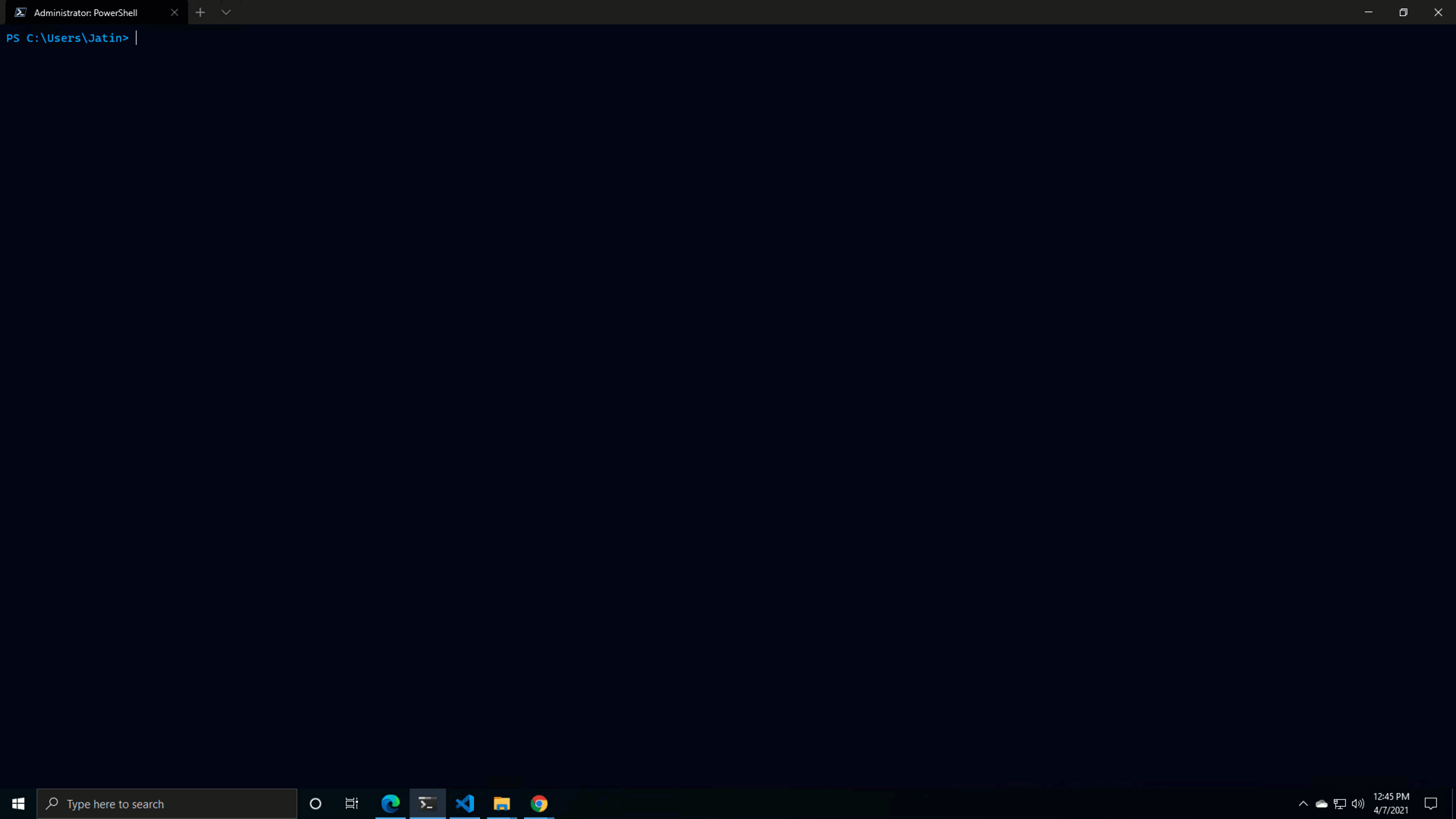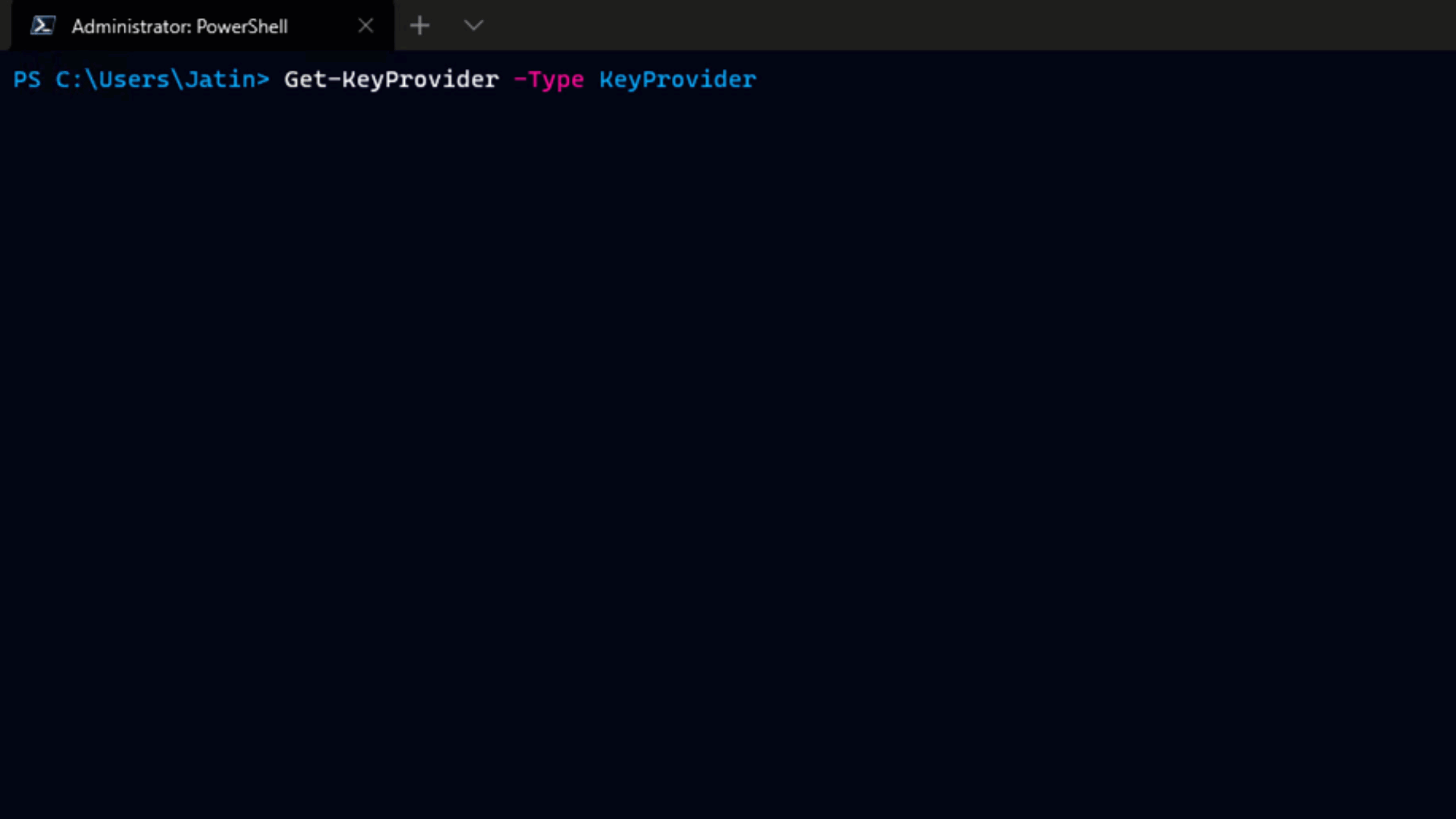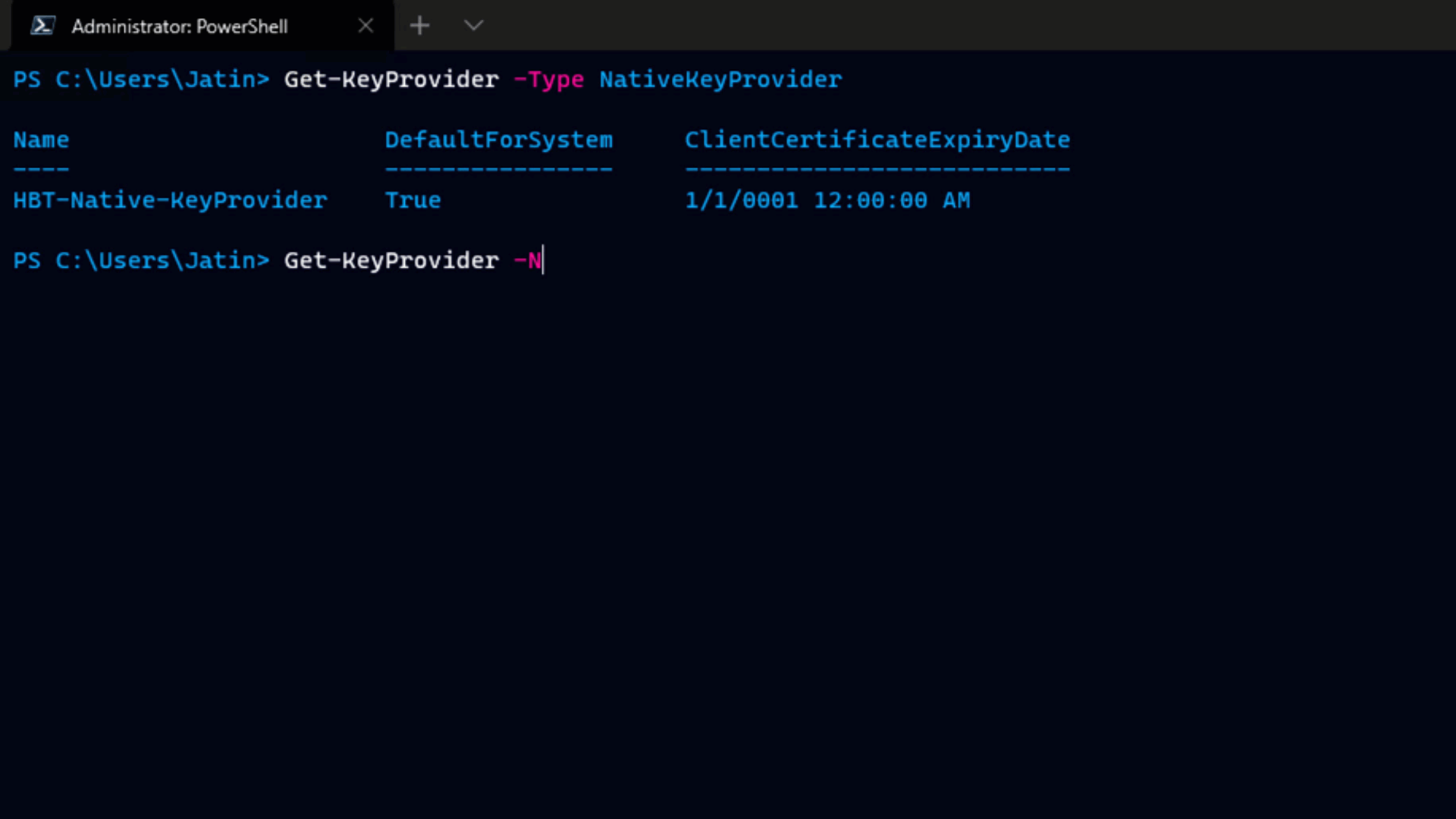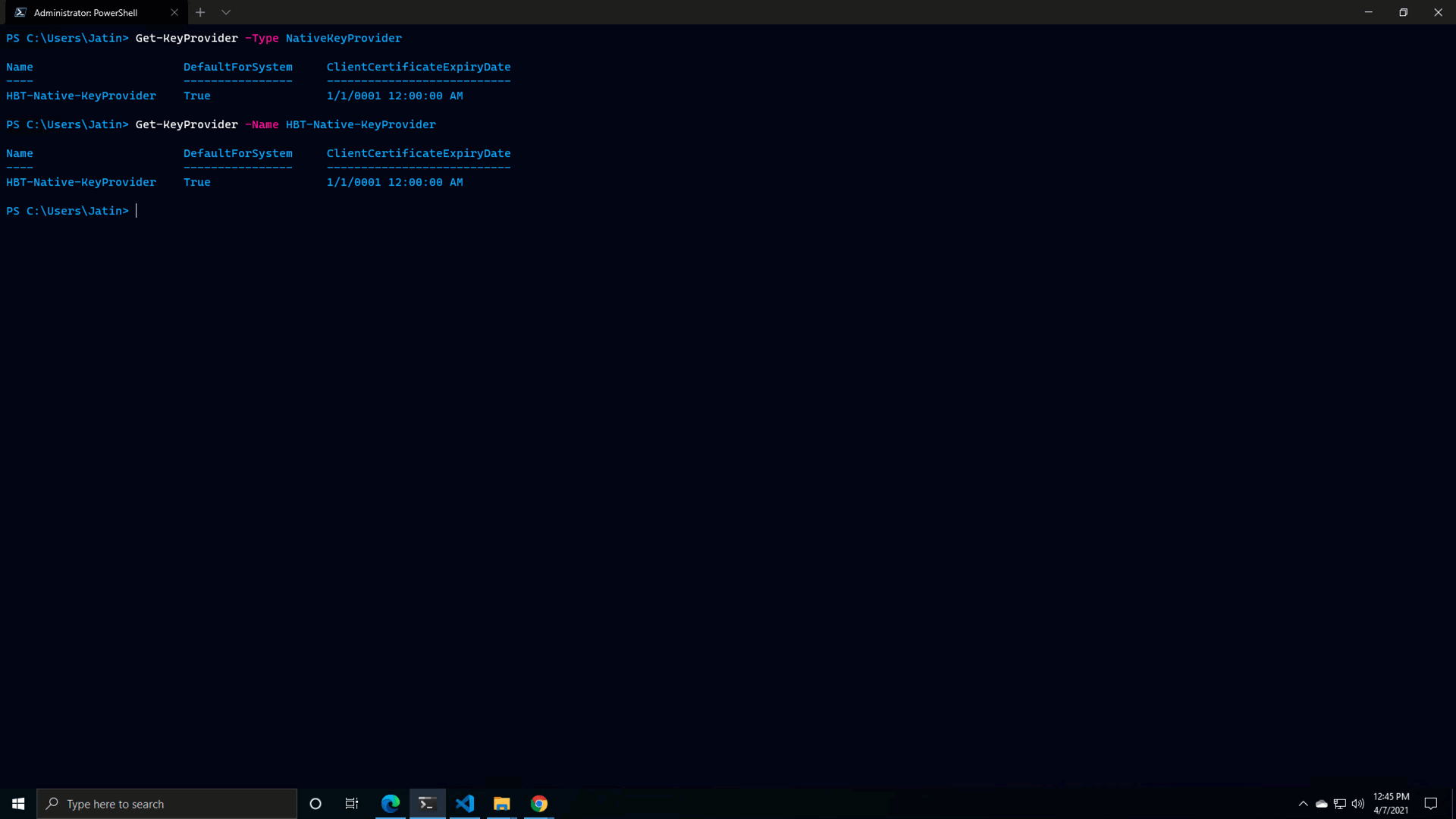
This property is a Dictionary, where all connected Pairings are stored. The Pairing is the VR API representation of the paired local and the remote sites. As we just authenticated only against the local VR site, the Dictionary contains only one entry. This is the local vCenter self-pair.
You can index this dictionary, by the vCenter name, and obtain certain Pairing object. You will need this Pairing object to invoke various operations from the VR API:
![]()
To authenticate against a remote vCenter Server, you will use another parameter set of the Connect-VrServer cmdlet. (Note that you must have a site pairing configured between the local and the remote vSphere Replication sites.). This time, for LocalServer parameter specify the already available VrServerConnection object. For RemoteServer parameter specify the name of the remote VC. For RemoteUser and RemotePassword parameters specify the user name and the password of the remote VC. Note that with VR we can have multiple remote sites configured:
$remoteVc = "myRemoteVcName"
$vrConnection = Connect-VrServer -LocalServer $vrConnection `
-RemoteServer $remoteVc `
-RemoteUser "administrator@vsphere.local" `
-RemotePassword "MyRemoteVCenterServerPassword"
Now, if you check the ConnectedPairings property of the VrServerConnection object, you will see that the dictionary contains second pairing, allowing you to invoke API operations on the remote site:
![]()
Alternatively you can authenticate against the local and the remote sites with a single Connect-VrServer call:
$remoteVc = "myRemoteVcName"
$vrConnection = Connect-VrServer -Server $localVr `
-User "administrator@vsphere.local" `
-Password "MyLocalVCenterServerPassword" `
-RemoteServer $remoteVc `
-RemoteUser "administrator@vsphere.local" `
-RemotePassword "MyRemoteVCenterServerPassword"
Configuring host based replication
For convenience, let’s store the remote site pairing that we will use for the replication in a variable:
$remotePairing = $vrConnection.ConnectedPairings[$remoteVc].Pairing
Retrieve the replicated VM
To start, you must retrieve the VM, which you want to replicate. Use the Invoke-VrGetLocalVms cmdlet, which requires PairingId and VcenterId parameters to be specified. We have these IDs with the Pairing object we stored in the $remotePairing variable:
$replicatedVm = Invoke-VrGetLocalVms -PairingId $remotePairing.PairingId `
-VcenterId $remotePairing.LocalVcServer.Id.Guid `
-FilterProperty 'Name' `
-Filter "VrSrmDemo"
You can also apply filter to this call. FilterProperty parameter specifies the VM property that will be used for the search. In this case this is the Name property. The Filter parameter specifies the property value, you are looking for. The result of this call is a VirtualMachineDrResponseList object, which contains list of VMs that match the specified filter. In our case this will be a list with one VM:
![]()
Configure VM’s HDDs for the replication
When configuring host based replication, you have to specify the VM’s hard disks that will be replicated. For each replicated disk you have to specify a datastore on the target VC. In this example we will replicate all the hard disks of our VM on one target datastore on the remote VC:
Retrieve the target datastore on the remote VC, using the Invoke-VrGetVrCapableTargetDatastores cmdlet:
$targetDatastore = Invoke-VrGetVrCapableTargetDatastores -PairingId $remotePairing.PairingId `
-VcenterId $remotePairing.RemoteVcServer.Id.Guid `
-FilterProperty "Name" `
-Filter "MyRemoteDS"
Here for VcenterId, specify the remote VC Id. Specify FilterProperty and Filter parameters to choose the target datastore by name.
Hard disks are available in the Disks property of our VirtualMachine object, stored in the $replicatedVm variable. Iterate over the Disks list and initialize ConfigureReplicationVmDisk objects for each hard disk. Store these configurations in $replicationVmDisks array variable:
$replicationVmDisks = @()
$replicatedVm.List[0].Disks | ForEach-Object {
$replicationVmDisks += Initialize-VrConfigureReplicationVmDisk -VmDisk $_ `
-EnabledForReplication:$true `
-DestinationDatastoreId $targetDatastore.List[0].Id `
-DestinationDiskFormat 'SAMEASSOURCE'
}
Configure Host Based Replication
First you have to initialize ConfigureReplicationSpec object. Besides various replication settings, we have to specify the disk replication configuration, stored in the $replicationVmDisks variable to the Disk parameter. You also have to specify the target VC Id and the Id of the replicated VM.
$replicationSpec = Initialize-VrConfigureReplicationSpec `
-Rpo 60 `
-NetworkCompressionEnabled:$true `
-MpitEnabled:$true `
-AutoReplicateNewDisks:$true `
-LwdEncryptionEnabled:$false `
-MpitInstances 1 `
-MpitDays 1 `
-Disks $replicationVmDisks `
-TargetVcId $remotePairing.RemoteVcServer.Id.Guid `
-VmId $replicatedVm.List[0].Id
Then use the Invoke-VrConfigureReplication cmdlet to configure the replication. For parameters, specify the PairingId and the ConfigureReplicationSpec object:
$task = Invoke-VrConfigureReplication -PairingId $remotePairing.PairingId `
-ConfigureReplicationSpec $replicationSpec
The result of the operation is a TaskDrResponseList object, which in our example contains list of one task. If you want, you can specify array of ConfigureReplicationSpec objects, and replicate multiple VMs with single call.
To wait until the replication configuration task completes, retrieve the task until its Status property equals to something different from ‘RUNNING’:
Invoke-VrGetTaskInfo -TaskId $task.List[0].Id
![]()
In the next chapter we will use cmdlets from the VMware.Sdk.Srm module to create protection group and recovery plan for the replication that we just created.
Connecting Site Recovery Manager with Connect-SrmSdkServer
To connect Site Recover Manager server use the Connect-SrmSdkServer cmdlet. Do not use the old Connect-SrmServer cmdlet, already available in the VMware.VimAutomation.Srm module, as it’s not compatible with the VMware.Sdk.Srm module cmdlets.
Site Recover Manager supports only one pairing between local and remote SRM sites. You can connect either only to the local site, or you can authenticate with the remote site vCenter server site in the same call. Since we will further create protection group and recovery plan we will choose the second option. Note that you must have a site pairing configured between the local and the remote SRM sites.
$srmConnection = Connect-SrmSdkServer -Server "MySrmAddress.com" `
-User "administrator@vsphere.local" `
-Password "MyLocalVcPassword" `
-RemoteUser "administrator@vsphere.local" `
-RemotePassword "MyRemoteVcPassword"
If we look at the SrmServerConnection object, returned from the Connect-SrmSdkServer cmdlet, we will see that it contains property named ConnectedPairing. In this case this is a single Pairing object that represents the pair between the local and the remote SRM sites. You will need this Pairing object for invoking various operations from the SRM API:
![]()
Creating protection group and recovery plan for host based replication
In this chapter we will use the host based replication that we configured earlier. First we will initialize HbrProtectionGroupSpec with the VM that we already replicated:
$hbrSpec = Initialize-SrmHbrProtectionGroupSpec -Vms $replicatedVm.List[0].Id
In this example we reuse the VM Id, we have stored in the $replicatedVm variable, as it’s consistent between the VR and SRM APIs. If you need to retrive the replicated VM with the VMware.Sdk.Srm module, use the Invoke-SrmGetReplicatedVms cmdlet:
$replicatedVm = Invoke-SrmGetReplicatedVms `
-PairingId $srmConnection.ConnectedPairing.PairingId `
-VcenterId $srmConnection.ConnectedPairing.LocalVcServer.Id.Guid `
-FilterProperty "Name" `
-Filter "VrSrmDemo"
Use the HbrProtectionGroupSpec object to initialize SrmProtectionGroupCreateSpec. For the ReplicationType parameter specify HBR:
$protectionGroupSpec = Initialize-SrmProtectionGroupCreateSpec -Name "SrmDemoGroup" `
-ReplicationType HBR `
-ProtectedVcGuid $srmConnection.ConnectedPairing.LocalVcServer.Id.Guid `
-HbrSpec $hbrSpec
Create protection group with the Invoke-SrmCreateGroup cmdlet:
$task = Invoke-SrmCreateGroup -PairingId $srmConnection.ConnectedPairing.PairingId `
-ProtectionGroupCreateSpec $protectionGroupSpec
Wait for the SRM task to complete:
$task = Invoke-SrmGetTaskInfo -TaskId $task.Id
When $task.Status is equal to ‘SUCCESS’, retrieve the protection group, using the $task.Result property, which contains the ID of the created group:
$protectionGroup = Invoke-SrmGetGroup -PairingId $srmConnection.ConnectedPairing.PairingId `
-GroupId $task.Result
To conclude this example we will create a recovery plan for the protection group. For that purpose first Initialize RecoveryPlanCreateSpec, required by the Invoke-SrmCreatePlan cmdlet:
$recPlanSpec = Initialize-SrmRecoveryPlanCreateSpec `
-Name "SrmDemoRecoveryPlan" `
-ProtectedVcGuid $srmConnection.ConnectedPairing.LocalVcServer.Id.Guid `
-ProtectionGroups $protectionGroup.Id
Then create the recovery plan with the RecoveryPlanCreateSpec object and wait for the task to complere, using the Invoke-SrmCreatePlan:
$task = Invoke-SrmCreatePlan -PairingId $srmConnection.ConnectedPairing.PairingId `
-RecoveryPlanCreateSpec $recPlanSpec
Invoke-SrmGetTaskInfo -TaskId $task.Id
Disconnect SRM and VR server connections
After you have finished interacting with the SRM server, close the connection, using the Disconnect-SrmSdkServer cmdlet:
Disconnect-SrmSdkServer "MySrmAddress.com"
To close the VR server connection use the Disconnect-VrServer cmdlet:
Disconnect-SrmSdkServer "MyVrAddress.com"
Conclusion
You can combine the VMware.Sdk.Vr and the VMware.Sdk.Srm PowerCLI modules to automate the end to end scenario of creating host based replication, and utilizing it with protection group and recovery plan. If you want to automate array based replication, available with the VMware.Sdk.Srm module, refer to the “Array Based Replication with PowerCLI 13.1” blog post. Also, you you can check out “vSphere Replication REST API with PowerShell: Configure VM replication“.
The post Managing SRM and VR with PowerCLI 13.1 appeared first on VMware PowerCLI Blog.




















 support
support












