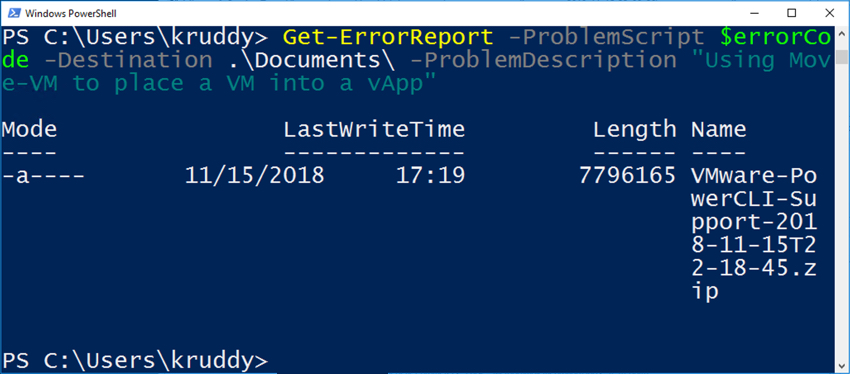
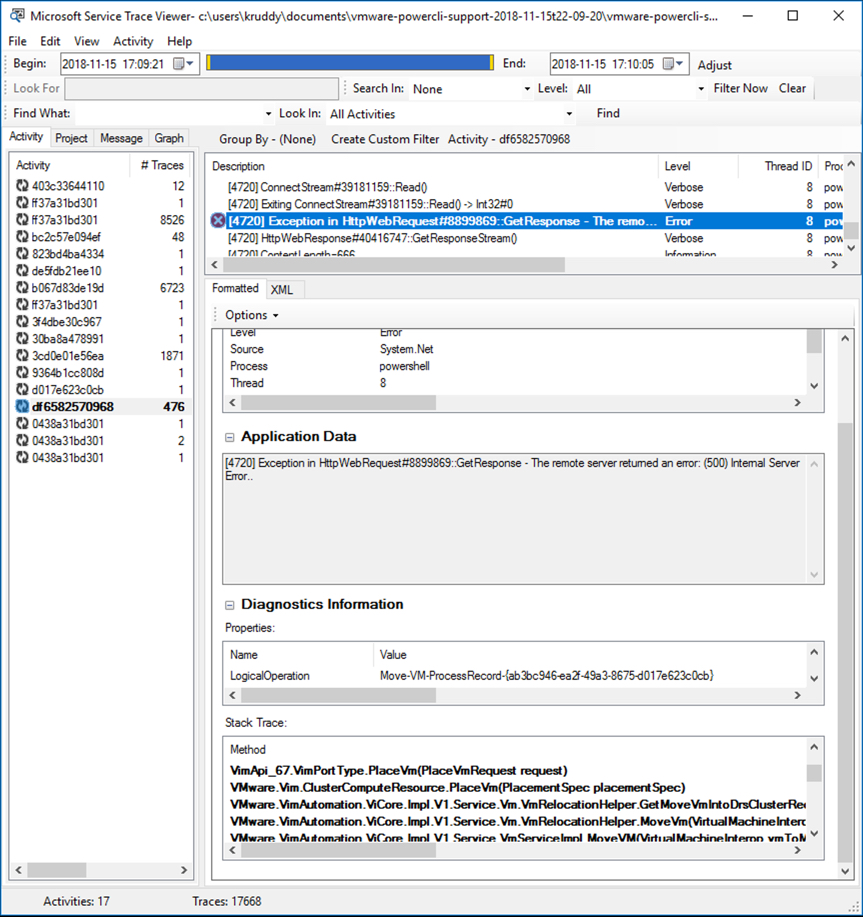
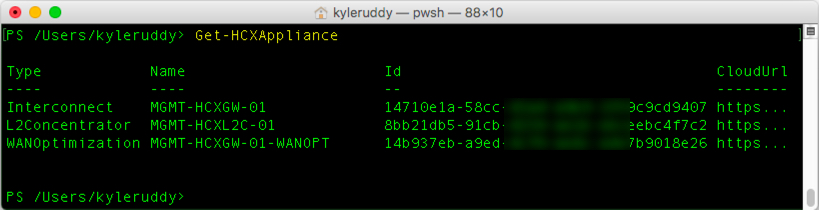
Did you know the vCenter Server Appliance (VCSA) has file-based backup options?
This ability was actually released in vSphere 6.5. However, there was one feature in particular that was missing: a scheduler. I’m happy to say that as part of vSphere 6.7, the VCSA received a backup scheduler!
Recently, my teammate, Emad Younis released a couple cool walkthroughs to the vSphere Central site to manage file-based backup and restore actions. Under the covers, both of these actions are served up by vSphere’s RESTful APIs and therefore PowerCLI can also be used to automate these actions! One other benefit of using the API, you don’t have to hand out the root credentials. Users with the ‘SystemConfiguration.Administrators’ permission are able to perform all of the following tasks through the API and PowerCLI!
To perform a file-based backup with PowerCLI, we’ll need to make use of the CIS module. Since the CIS module is a low-level module, let’s see a couple examples of this in action.
Create a File-Based Backup
Let’s first start with the process to perform a backup.
First step, log in to the CIS Service for the VCSA:
Connect-CisServer -Server vcsa01.corp.local
Next, we need to find the appropriate service to perform a backup:
Get-CisService -Name *backup*
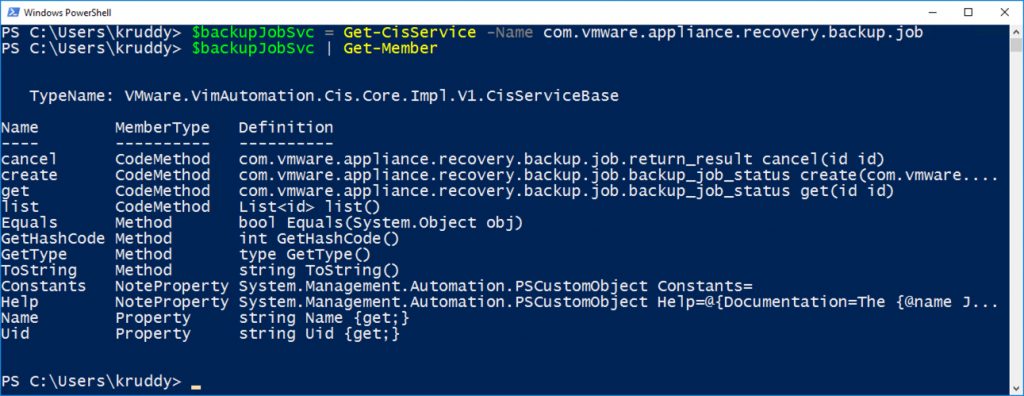
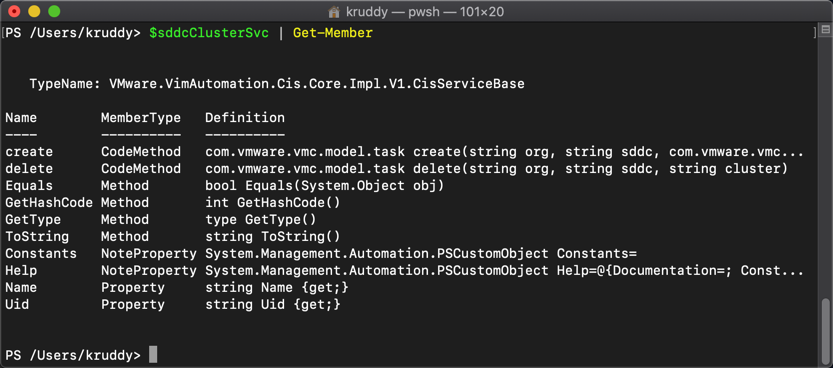
Based on the output, we will want the ‘com.vmware.appliance.recovery.backup.job’ service. We will store that into a variable so we can easily interact with that specific service. To see the method we are going to use, take that variable and pipe it to ‘Get-Member’.
$backupJobSvc = Get-CisService -Name com.vmware.appliance.recovery.backup.job $backupJobSvc | Get-Member
As part of the respose, we’ll see two important items. First, the ‘create’ method which we’ll use to actually create the backup job. Second, the ‘Help’ property. We can use ‘Help’ to help us form the input for the backup job with the following command:
$backupJobSvc.Help.create.piece
We can now fill in each of the parameters with information for our environment. There are a couple caveats here. First, the ‘parts’ parameter is expecting an input of an array type. Second, each of the password parameters require a special type in order to be accepted.
$backupSpec.parts = @("common")
$backupSpec.location_type = "FTP"
$backupSpec.location = "ftp01.corp.local"
$backupSpec.location_user = "backup"
[VMware.VimAutomation.Cis.Core.Types.V1.Secret]$backupSpec.location_password = "VMware1!"
$backupSpec.comment = "PowerCLI Backup Job"
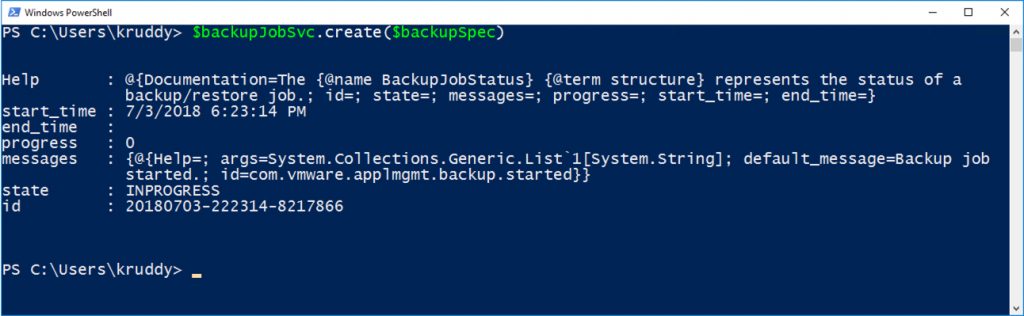
Finally, having input all of our information, we can create the backup job!
$backupJob = $backupJobSvc.create($backupSpec)
We can combine this into a nice script as follows:
# Login to the CIS Service of the desired VCSA
Connect-CisServer -Server vcsa01.corp.local
# Store the Backup Job Service into a variable
$backupJobSvc = Get-CisService -Name com.vmware.appliance.recovery.backup.job
# Create a specification based on the Help response
$backupSpec = $backupJobSvc.Help.create.piece.CreateExample()
# Fill in each input parameter, as needed
$backupSpec.parts = @("common")
$backupSpec.location_type = "FTP"
$backupSpec.location = "ftp01.corp.local"
$backupSpec.location_user = "backup"
[VMware.VimAutomation.Cis.Core.Types.V1.Secret]$backupSpec.location_password = "VMware1!"
$backupSpec.comment = "PowerCLI Backup Job"
# Create the backup job
$backupJobSvc.create($backupSpec)
Create a Scheduled File-Based Backup
Let’s now take a look at creating a scheduled backup job with PowerCLI.
Following a similar process to the last task, we will want to use one of the services we found previously called: com.vmware.appliance.recovery.backup.schedules
This time, we see two inputs are required. First, the schedule ID. Second, the specification which is similar to the prior example. The ‘Help’ property will be quite useful to create both specifications.
Much like the prior example, this one too has some caveats. The Schedule ID input can be a string of your choosing. For reference, performing this process in the UI creates a default ID of ‘default’. The scheduling recurrence configuration can be done in many ways through the ‘days’ property. If a daily backup is desired, there’s no need for any input and it can be left ‘unset’. If a specific day/s are desired, the input has to be of an array type.
Here’s a script which can be used to create a scheduled file-based backup:
# Store the Backup Job Service into a variable
$backupSchedSvc = Get-CisService -Name com.vmware.appliance.recovery.backup.schedules
# Create a Schedule ID specification based on the Help response
$schedSpec = $backupSchedSvc.Help.create.schedule.Create()
$schedSpec = 'weekly'
# Create a specification based on the Help response
$backupSchedSpec = $backupSchedSvc.Help.create.spec.Create()
$backupSchedSpec.parts = @("common")
$backupSchedSpec.location = "ftp://ftp01.corp.local"
$backupSchedSpec.location_user = "backup"
[VMware.VimAutomation.Cis.Core.Types.V1.Secret]$backupSchedSpec.location_password = "VMware1!"
$backupSchedSpec.enable = $true
$recurSpec = $backupSchedSvc.Help.create.spec.recurrence_info.Create()
$recurSpec.days = @("Sunday")
$recurSpec.minute = '59'
$recurSpec.hour = '23'
$backupSchedSpec.recurrence_info = $recurSpec
$retentSpec = $backupschedsvc.help.create.spec.retention_info.Create()
$retentSpec.max_count = '5'
$backupSchedSpec.retention_info = $retentSpec
# Create the backup job
$backupSchedSvc.create($schedSpec, $backupSchedSpec)
Afterwards, if you log into the VCSA Appliance Management Interface (VAMI), your backup schedule should look much like the following:

Summary
The ability to create file-based backups of your vCenter Server is a function that is only available to the VCSA. This function is made possible by a set of RESTful APIs which PowerCLI can also consume, with the additional benefit of not being reliant on the root account! This blog post walked through examples of creating a file-based backup job and creating a scheduled file-based backup job.
More information about VCSA file-based backup can be found on the vSphere Central site: vCenter Server Appliance 6.7 File-Based Backup
Let us know in the comments how you’re automating your VCSA backups!
The post Automating File-Based Backups of vCenter Server Appliance appeared first on VMware PowerCLI Blog.